A Cyber attack is usually indiscriminate, no matter how small or large the target, you are still at risk of one.
However, when larger companies experience Cyber attacks, they are a lot more public and easy to notice.
In this blog, we’ll focus on a very recent attack that Acer suffered.
Details on the Cyber attack
Acer Inc., a major global technology company based in Taiwan, is facing a potential data breach from a hacker going by the alias “Kernelware.”
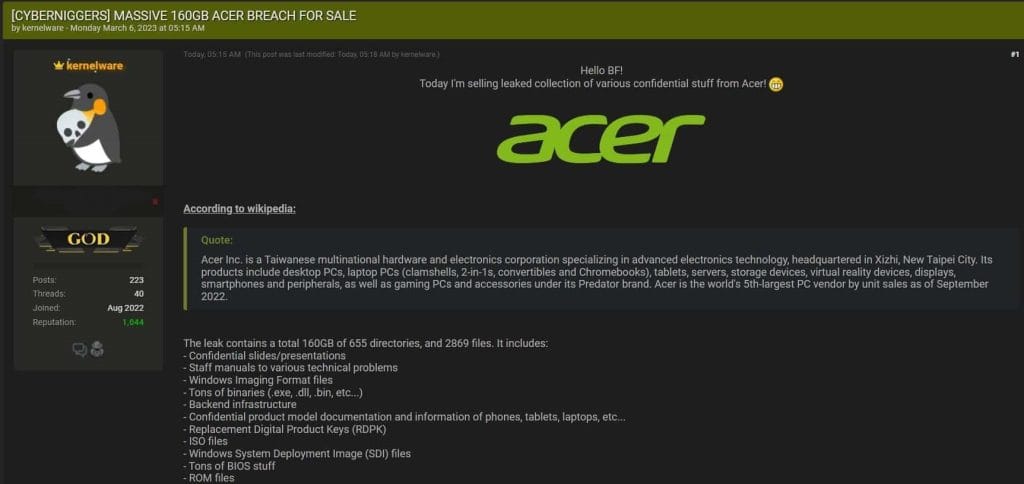
The hacker is claiming responsibility for a major data breach at Acer Inc.
According to Kernelware, the alleged breach occurred in mid-February 2023.
Furthermore, it was claimed that the end result of the theft was a vast amount of sensitive information. This totalled 160GB of 655 directories and 2869 files.
The motive for this?
In a post on a hacker forum, Kernelware offered to sell the data to interested parties, saying that it contained a wide range of valuable files and documents.
The hacker also shared a sample of the stolen data to prove its authenticity.
Here is a screenshot of the statement from Kernelware themself:
As evident from the screenshot, this Cyber attack’s only motive was money, this is very common for most attacks on the internet yet other possibilities can never be ruled out.
Acer’s response?
On the other hand, the response to a Cyber attack is just as important as the preparation preparing for one. So, let’s take a look at how Acer dealt with this attack in particular.
“We have recently detected an incident of unauthorized access to one of our document servers for repair technicians. While our investigation is ongoing, there is currently no indication that any consumer data was stored on that server,” an Acer spokesperson stated.
However, the stolen information could be used by Cyber criminals for various purposes, including blackmail, identity theft, and fraud.
Additionally, the exposure of Acer’s backend infrastructure and product models could reveal vulnerabilities that could be exploited by other attackers.
This does question exactly what Acer is planning to do in the future to combat this attack, and if there will be any more breached information that comes to light.
Our conclusion
As always, individuals and organizations are advised to take measures to protect their sensitive data and systems.
This includes using strong passwords, implementing multi-factor authentication and keeping their software and firmware up-to-date.
This is because the threat of data breaches and Cyber attacks is ongoing and evolving. Requiring constant vigilance to mitigate the risks.
Furthermore. that’s why at Solutions 4 IT we can’t recommend enough that you have someone in-house or outsourced externally to look after your Cyber security and IT Support needs.
That, is the end of our blog on Acer’s most recent Cyber attack. We hope you’ve found this blog informational and interesting.
If so, be sure to stay up-to-date on our latest blog releases, ranging from IT News blogs to Knowledgebase articles. Thank you for reading!